Monero (the Esperanto word for “money”) is a cryptocurrency built on the principles of non-connectivity and untraceability. This means that you cannot link two Monero transactions and determine the source or destination of funds.
This is the interesting feature of Monero. It continues to use blockchain to track the movement of funds, but uses cryptography to hide the source, amount, and destination of transactions. Let’s explain these features by comparing them with the Bitcoin registry, which looks like this:
In contrast, the Monero blockchain looks like this:
We’ll talk about how this kind of concealment is possible in a moment.
Brief history of Monero
Monero was forked from the privacy-focused cryptocurrency Bytecoin, launched in 2012. Bytecoin is the first protocol based on the open source technology CryptoNote, which aims to solve some of the problems in Bitcoin. These issues are ASIC mining (using specialized mining hardware) and lack of privacy in transactions. CryptoNote is now the basis of many cryptocurrencies that aim to be privacy-oriented.
In 2014, dissatisfied with the initial release of Bytecoin, developers forked the network, creating a new project known as Bitmonero. Later, the name was changed and the “Bit” part was discarded, resulting in today’s Monero.
How does Monero work?
When you browse Monero, you’ll come across terms like “ring signature” and “stealth address”. These are two key innovations that enable the anonymity of Monero transactions. In this section, we will examine both concepts in detail.
Ring signatures and Confidential Transactions
A ring signature is a digital signature created by a person in a particular group. Anyone who has the signature and the public keys of the group members can verify that the signature belongs to one of the participants. However, it cannot identify which participant it is.
The 2001 article How to Leak a Secret, which discusses this structure in detail, uses the example of a government cabinet. Suppose a member of this cabinet – Bob – has incriminating evidence against the Prime Minister. Bob wants to prove to a reporter that he’s a cabinet member, but he also wants his identity to remain anonymous.
Bob cannot do this with standard digital signatures. Anyone who compares the digital signature with its public key can conclude with certainty that the signature was created by Bob’s private key. So Bob could face serious consequences for leaking the prime minister’s actions. However, if the signatures of other cabinet members are used in the public signature scheme, it is not possible to determine who sent the message. However, it is still possible to say that the information was shared by a cabinet member, so that the accuracy of the information is proven.
This technique is used each time you create a transaction, giving you reasonable deniability. As your Monero wallet creates it, it pulls the keys of other users on the blockchain to create a ring. These keys act as bait – to an observer, transactions appear to be signed by anyone in the ring. As a result, there is no way for an outsider to determine whether the output is spent. At best, they can infer that one of the eight outputs in the image below may have been spent. The number of fake outputs is called mixin.
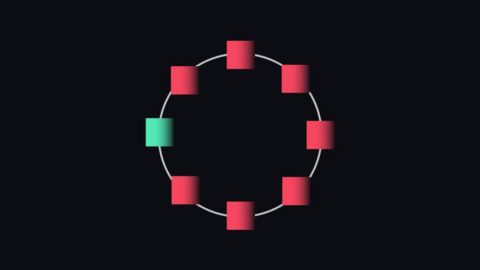
The green output in the image above is what you actually spent, the reds are the baits you get from the blockchain. For an observer, you may be spending any of these eight outputs.
In the past, the outputs included in the ring all had to be the same size. Because the transaction amounts were visible, it was easy to understand what was going on otherwise. For example, you could only have a ring of 2 XMR or 0.5 XMR outputs.
The upgrade to RingCT (Ring Confidential Transactions) changed this and included confidential transactions, a technique where transaction amounts are hidden. Integrating Confidential Transactions into the Monero protocol was a major advance in privacy as it eliminated the need to use outputs of the same size. Now you can create a ring of different sized outputs without revealing any information that could be used to deprive you of your anonymity.
Hidden addresses
Public signatures hide where the funds are coming from, but with standard public addresses it is still possible to see where the funds are going. This can be a problem if your ID is linked to one of your blockchain addresses.
Let’s say you use the same address on every order for your e-commerce store. Anyone placing an order can see the balance you have and tell others that this is your company address. This can also make you a target.
Confidential addresses hide where funds will go. It achieves this by having the sender create a one-time address based on its public address for use only in this transaction. The full address might look something like this:
41mT1gUnYHK6mDAxVsKeB7SP9hVesbESbWcupd7mMYC73GL4nSgsEwTGKHGT7GKoSEdMKvs8Fdu1ufPJbo5BV4d1PfYiEew
If you search for the address in the Monero block browser, you may find that you cannot bind any transactions to this address. This is because when a sender wants to send you funds, it creates a secret address by performing mathematical operations based on the address above. When they send XMR, they send it to a new address on the blockchain. Each address created will be different from the previous one and it will not be possible to associate these addresses with each other.
However, there are two pieces of information you can use: the private viewing key and the secret spending key. As the name suggests, the view key allows you to view all transactions associated with your address. You can share this address with others (for example, with your accountant) so that they can audit the funds you receive. The spend key is the key that is normally your private key – you use it to spend your coins.
Monero has a privacy policy by default, so you can’t choose not to use a private address. In this case, although the public ledger is automatically hidden, you can make your transactions visible to your preferred parties if you wish.
Next Page: What is the difference between Monero and Bitcoin?
Visits: 174









